2019 is the year of DAOs – Now we urgently need robust Consensus protocols for the People

1. Introduction
Summer of 2018 marked a disastrous moment for blockchain enthusiasts. Remembered as the Black Friday in the history of blockchain, that was the time of crashed crypto prices, declined ICOs and disruption of the crypto bubble. Since then we have witnessed the brutal implementation of Darwin’s Law. The blockchain market healed itself, refrained from weak (and bogus) projects while projects with substance and a strong technological vision survived. There is also much evidence that these kind of projects solving a sophisticated technical challenge and contributing with a solution to affirm decentralization get the support of the community. Although ICOs have been condemned as “dead” after the market crash, projects with strong deep tech vision received nevertheless a descent amount of fundings from the community. Most notable are the ICOs of Fetch.AI and Ocean Protocol raising 6m and 1.8m USD, respectively. Far away from the craze of the past, these are fair numbers for early-stage ventures to showcase the viability of their technology and to prove a product-to-market fit.
2. The Opportunity — DAOs
After the storm comes the sun. 2019 is full of positive energy and innovation. Much hope is given to projects related to Decentralized Autonomous Organizations (DAOs). They lift the core principles of blockchains — decentralization, incentivization and democratization — to the next level. Instead of machines agreeing on the global state of the network, humans agree through a democratic decision on the next state of the community. This idea disrupts the way organisations, governments or enterprises are operated and executed. Consider, for example, a DAO where
- devs working within an open source project vote on the integration of code proposals, this way overcoming the interests of a central project owner that tends to guide the development into a direction believing to do right things but his decision stands in sharp contrast with the interests of the community. The mission pursuits, for example, the ditcraft.io project.
- fans of a soccer club vote on the budget spent on new players and coaches, this way realizing the dream of governing “their” club instead of accepting the choices of oligarchs who own the club.
Philosophically and technically DAOs implement the very powerful notion – disruption of centralization – with the slight difference that the central parties are rather human authorities, governments or owners. Against this background decentralized autonomous organisations have all what it takes to become the next killer application on top of a blockchain network.
3. The Challenge – Voting Schemes on the Blockchain
At the protocol layer, blockchain networks and DAOs have also much in common.
What a consensus protocol is for blockchain nodes, a voting protocol is for DAO participants.
In fact, one can call a voting scheme a consensus with the additional property of voter privacy. The additional privacy property is necessary to safeguard that the choices made by each voter are taken independently and anonymously. The latter is a prerequisite of the first property and protects voters against rebounds after the ballot.
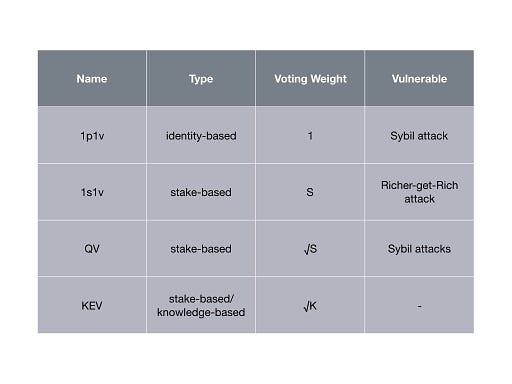
There are a handful of voting protocols for permissionless blockchains. Yet some research is required to verify their suitability for DAOs.
3.1. The One-Person-One-Vote (1p1v) protocol
Known as the mother of voting mechanisms, the one-person-one-vote scheme is the preferred method to reach a consensus in matters of governance (eg. presidential elections). The scheme permits each eligible voter to cast a vote. Typically a trusted third party (eg. delegates of the government) manage and orchestrate the election. They safeguard the voting follows a protocol of conduct. Once the voting period ended, they count the votes and announce the result following a majority quorum.
One might be tempted to adapt 1p1v to the blockchain setting. However there are problems with that. In a permissionless network wallet addresses serve as the only means to identify a voter. As long as no identity layer is in place to link the addresses with real-world identities, 1p1v falls prey to Sybil attacks. In a Sybil attack a malicious voter simply creates multiple wallet addresses, each permitting him to cast a vote in a ballot. Due to the permissionless nature of the blockchain network, such attacks are unavoidable and hence make 1p1v schemes unsuitable for voting schemes.
1p1v is an unsuitable voting mechanism in permissionless blockchains (as long as no identity layer is in place).
3.2. The One-Stake-One-Vote (1s1v) protocol
One-stake-one-vote schemes are the de-facto standard mechanism for votings in permissionless setting. Inspired by proof-of-stake consensus protocols and the fact that a naive adaption of 1p1v to the blockchain fails in a 1s1v protocol each voter deposits a stake. The number of staked tokens weights his vote. The quorum is defined over the decision with majority stake and the stake of the minority is slashed.
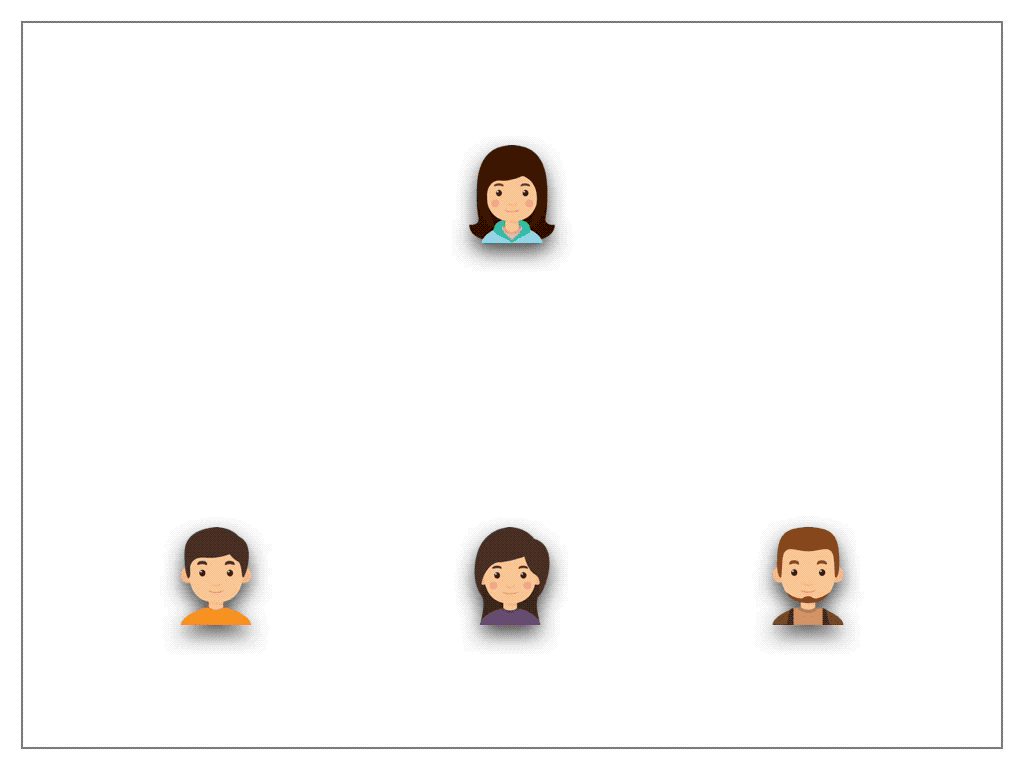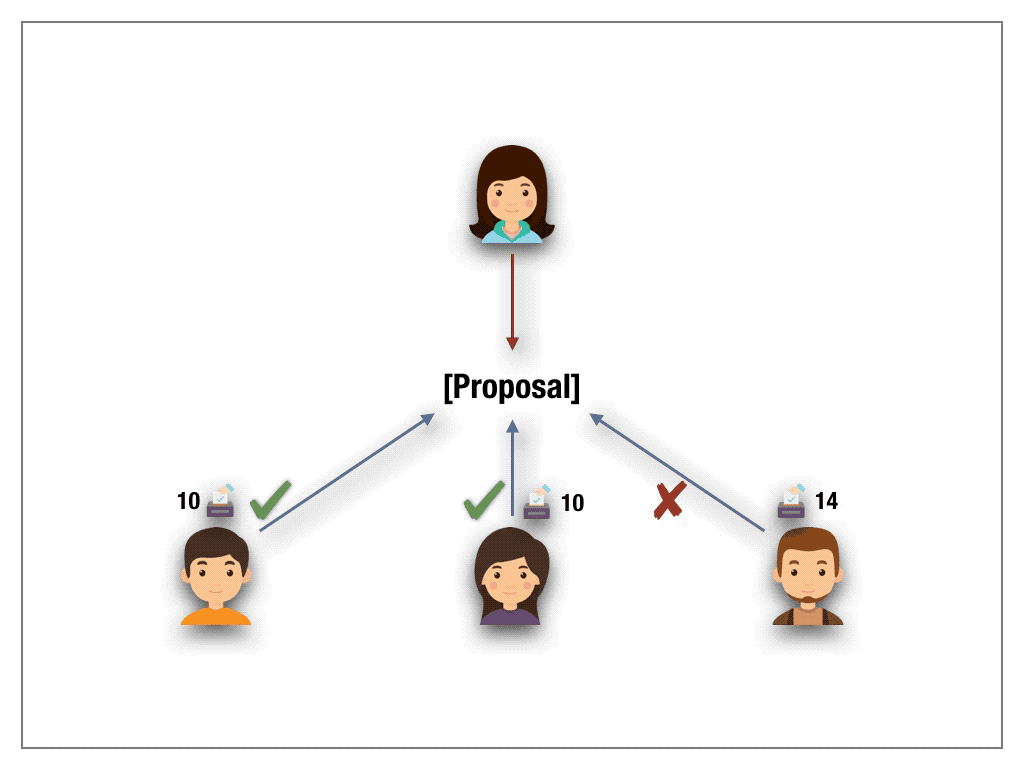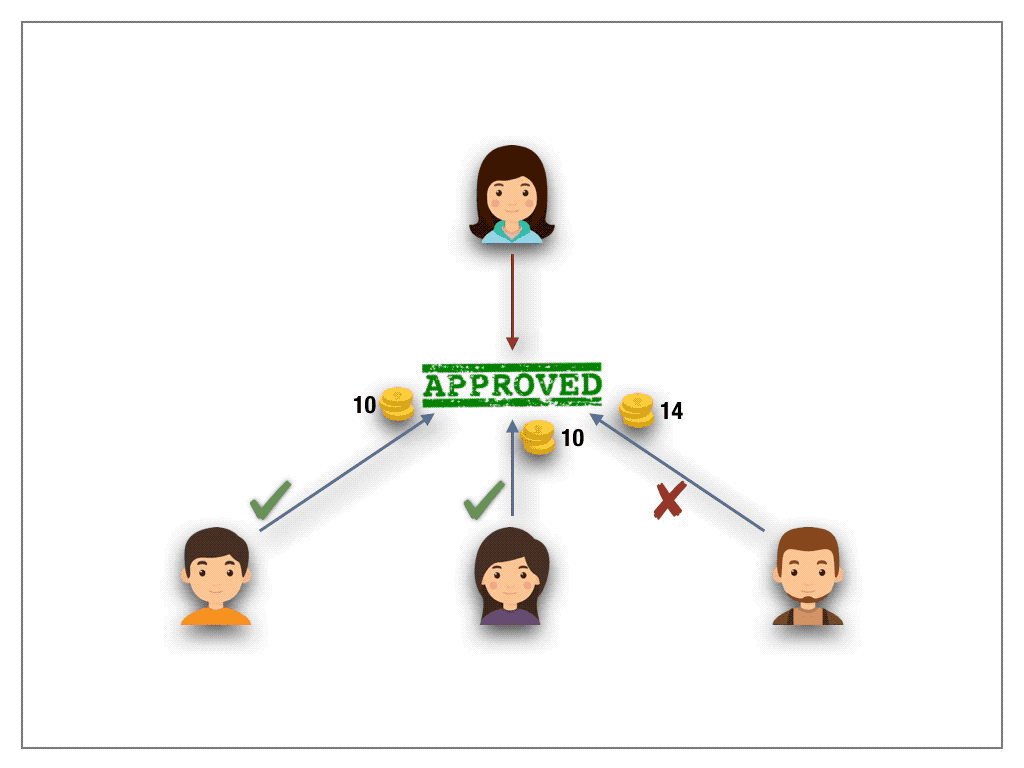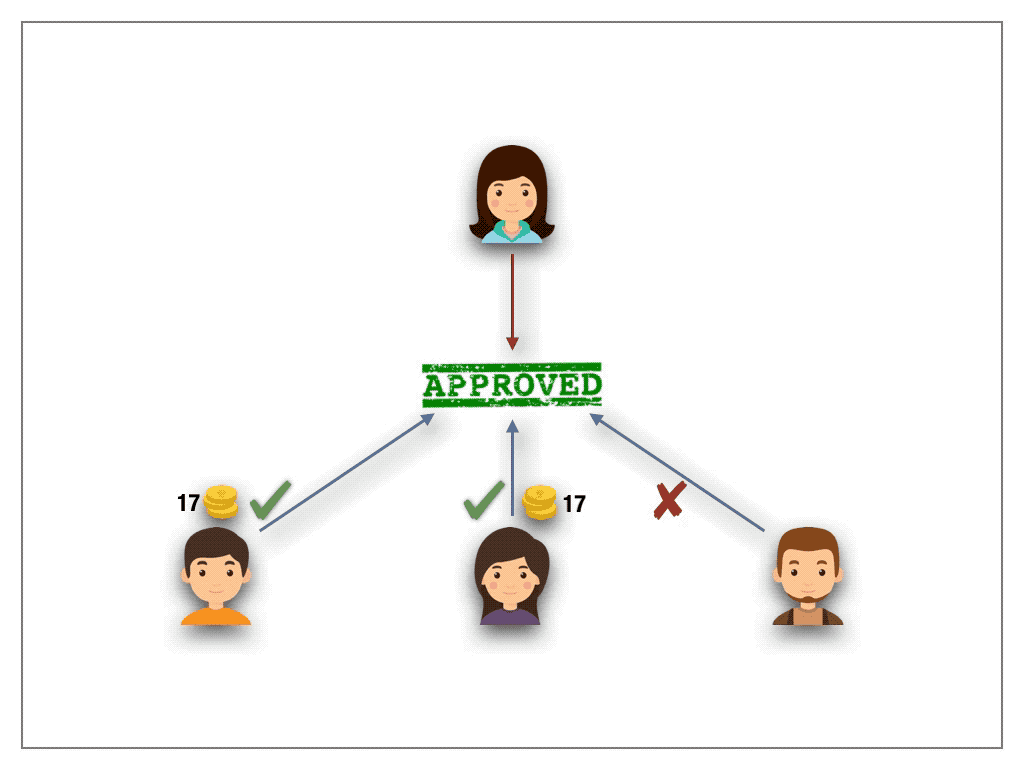
1s1v must be considered with care, as the protocol can harm the democratic choice in DAOs. Though 1s1v remedies the problem of Sybil attacks in 1p1v schemes (there is simply no need anymore for the creation of multiple addresses as the size of the stake dictates the voting power) a new weakness arises. The protocol gives financial oligarchs, that rich voters able to put forth high stakes, a non-negligible advantage to game the outcome of the ballot. In fact, they can hijack the voting mechanism by overstaking all (minority) voters and collect their shares. Such a “voting bot” can easily be automated and be used not only to contaminate the notion of democracy, but also to harvest the stakes of honest voters. One might be tempted to assume limiting the total amount of stake per voter might solve the vulnerability. By casting a Sybil attack an oligarch still can game the outcome of the ballot and thus hijack the protocol.
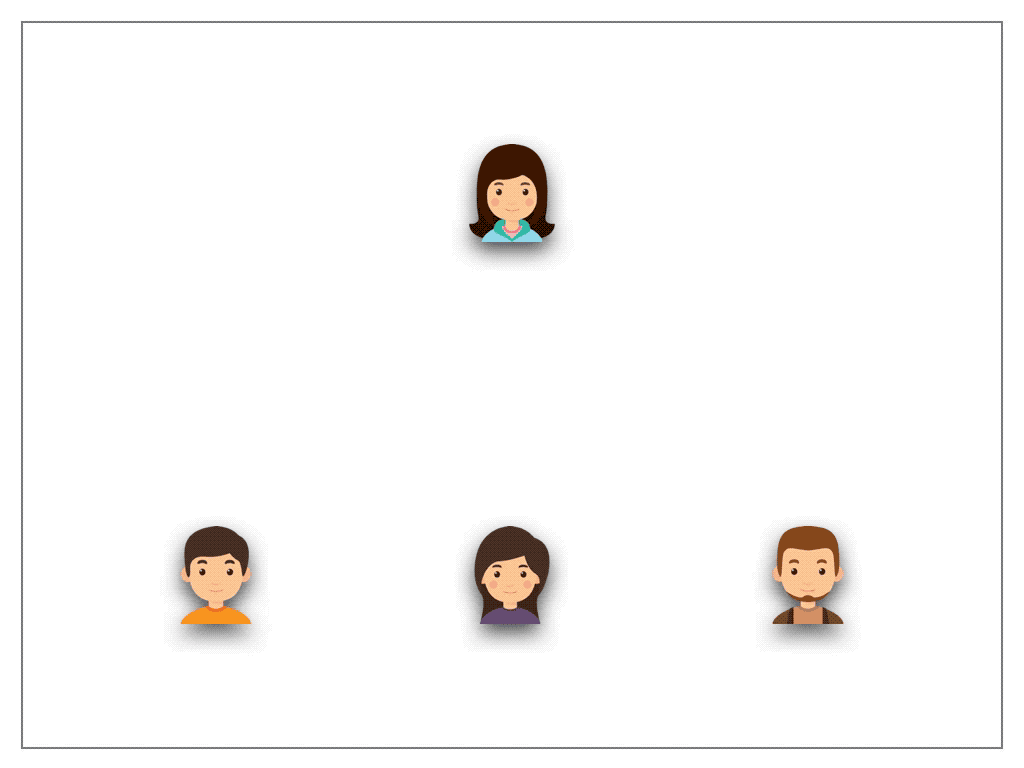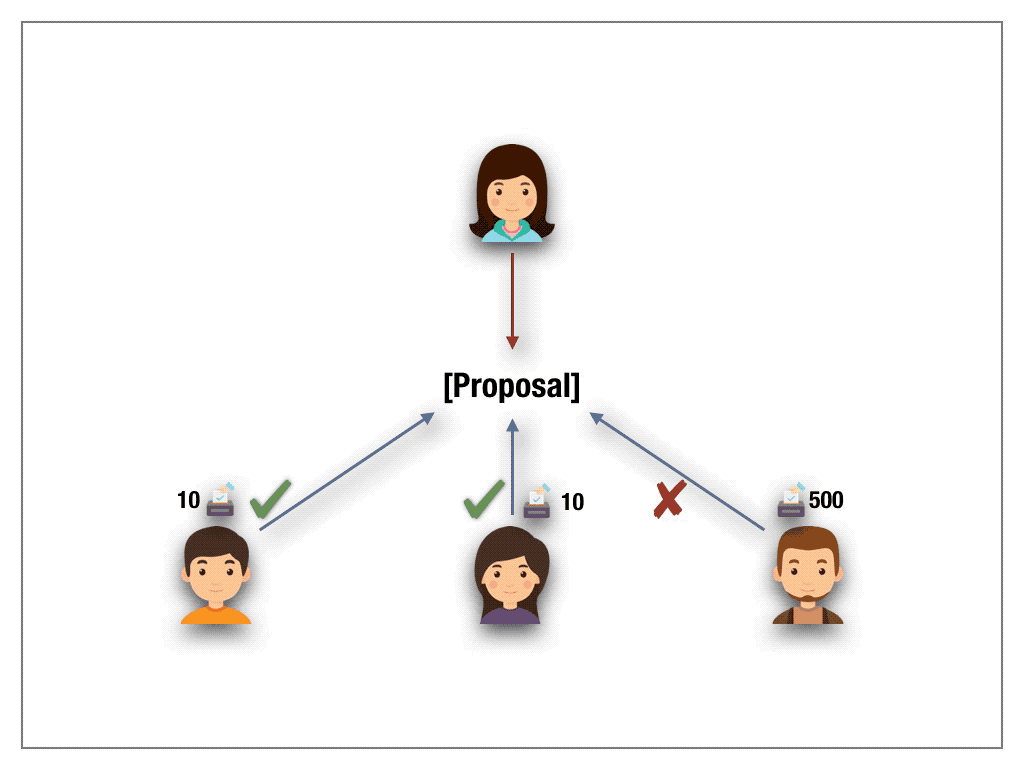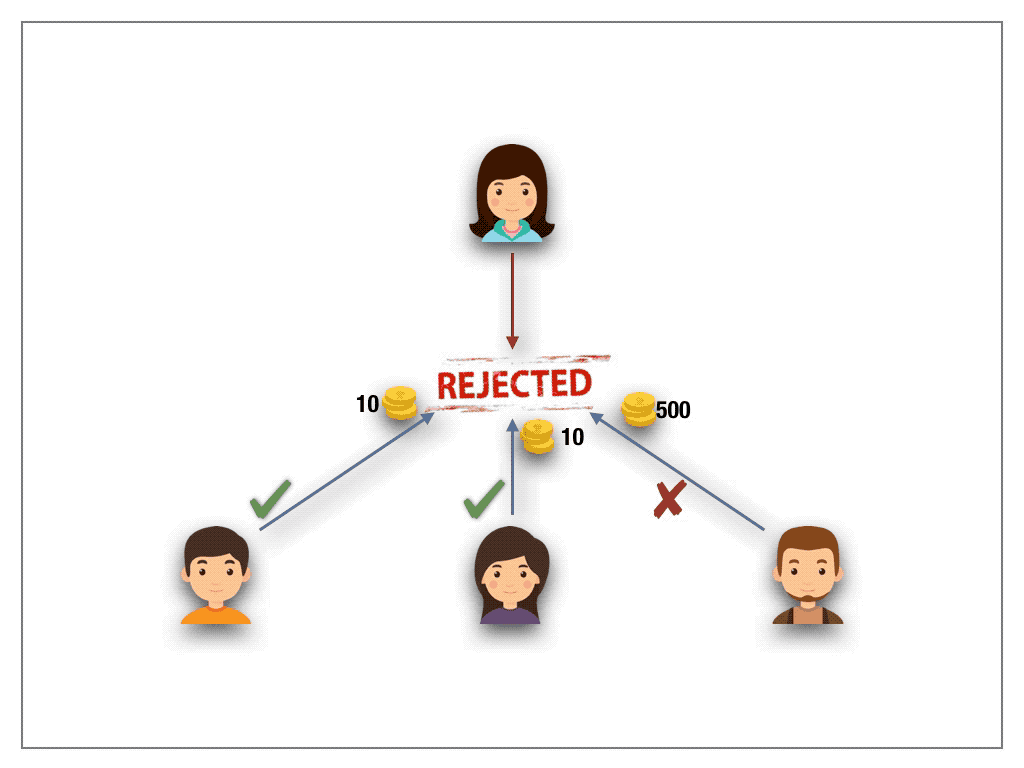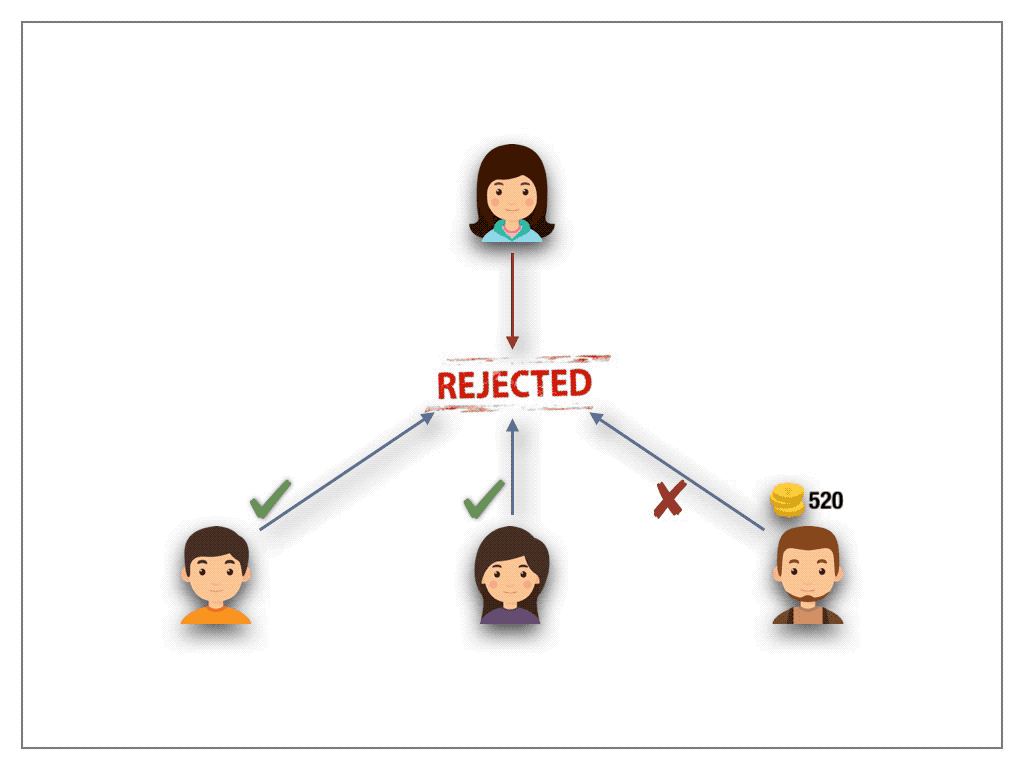
3.2 Quadratic Voting (QV) protocol
A radically new idea was proposed by Steven Lalley and Glen Weyl to mitigate the problem of unfair wealth distribution. The authors put forth the beautiful notion of Quadratic Voting. Their idea is based on buying votes. A bit more precise, each voter can buy as many votes he wishes by paying the tokens in a fund with one caveat. The voter has to pay quadratically in the number of votes. The money is then returned to voters on a per capita basis. Suppose, for example, a voter intends to cast 10 votes. Then he pays 10²=100 tokens to acquire the votes. On a high level, the quadratic pricing function acts like a wealth slow down mechanism. Lalley and Weyl have proven under certain assumptions QV to be a mechanism against a tyranny of majority stake holders.
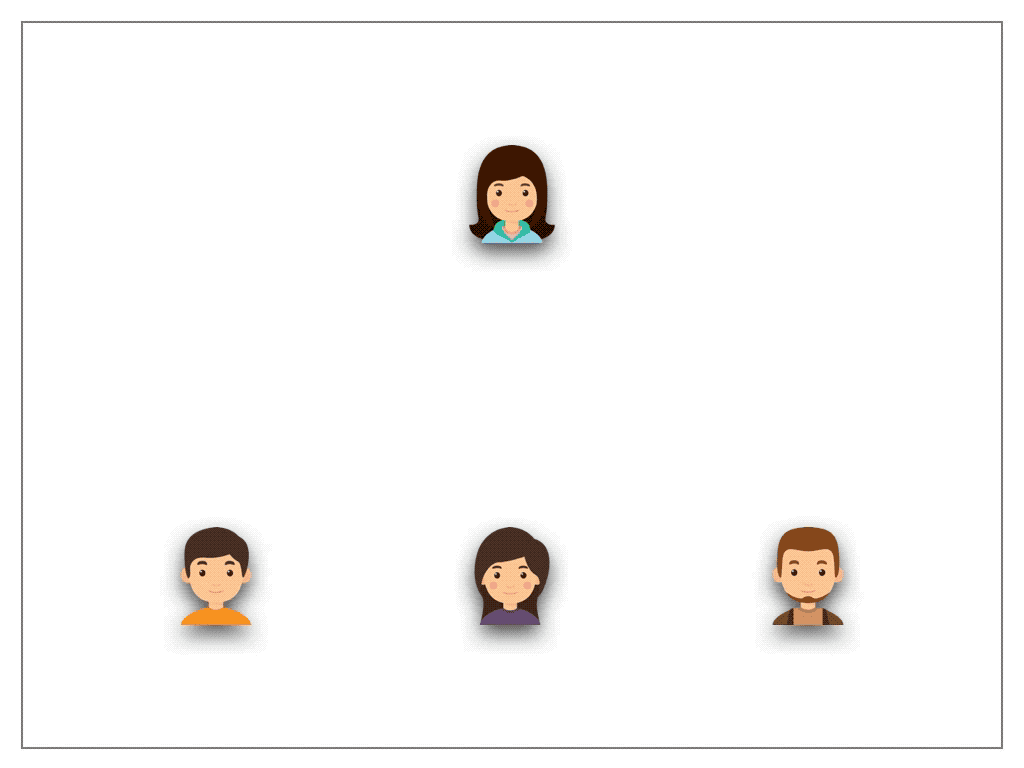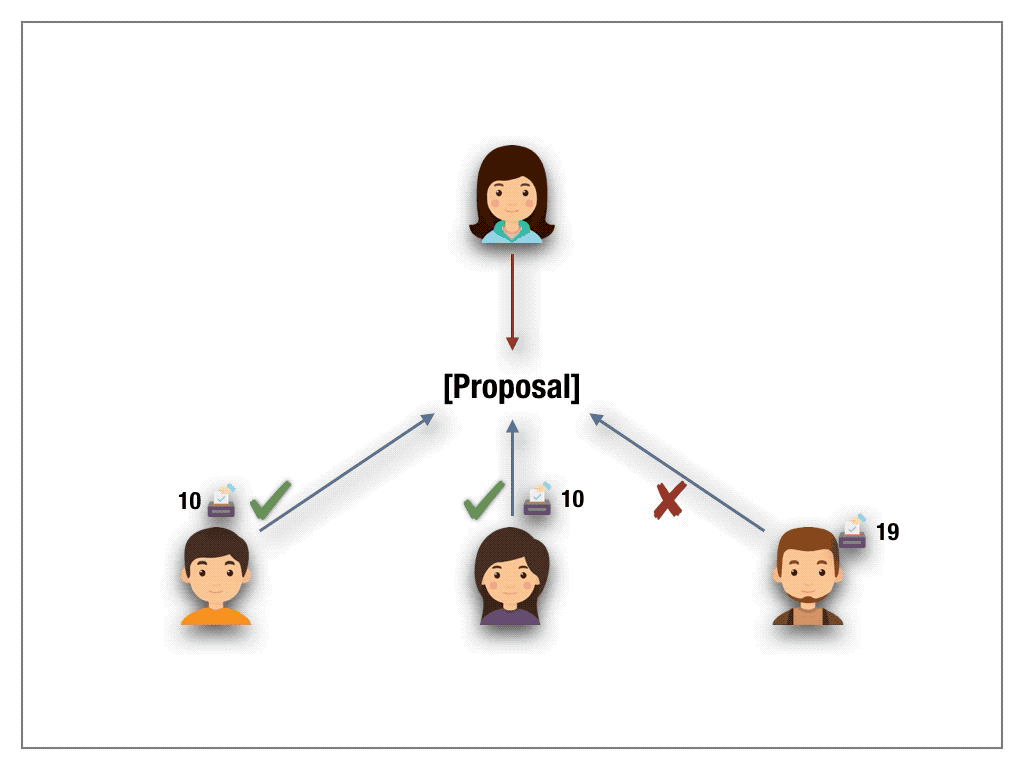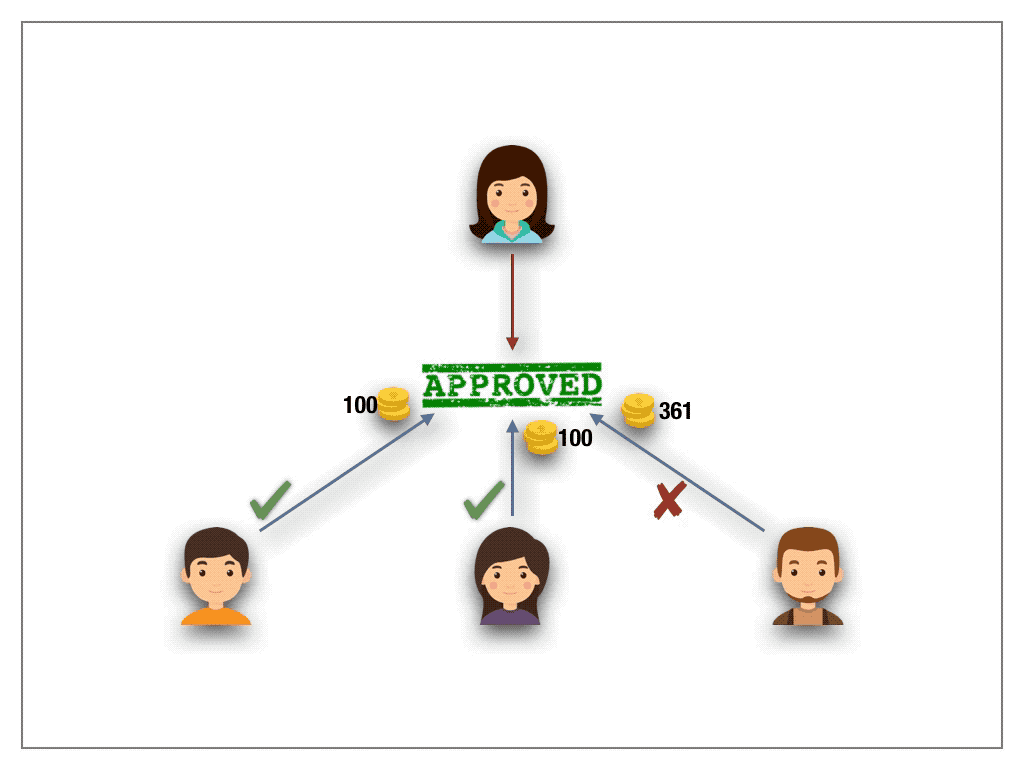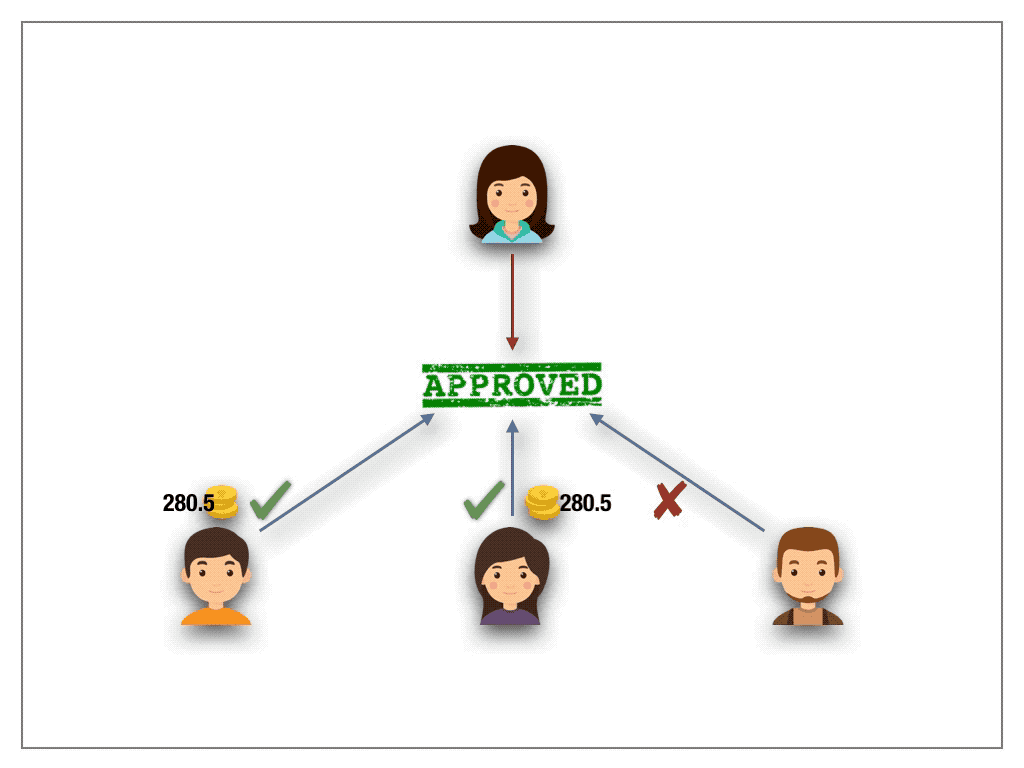
While their results apply to real-world decision makings, transferring the scheme to the permission-less blockchain setting does not carry over with the expected outcome. The problem with the blockchain world are Sybil attacks. The design of blockchain technologies allows a voter to cast many anonymous identities. Hence, to accumulate 10 votes, the sybil attacker simply creates 10 accounts under different identities. This way, the attacker requires 10 tokens in total to cast 10 votes. However, we would like to stress that QV may satisfy the desired outcome in the case of permission-based settings where the identities of the players are known and fixed in advance throughout the lifetime of the system(For example a proof of authority based system).
QV protocols are susceptible to Sybil attacks.
3.4. Knowledge-extractable Voting (KEV) protocol
Inspired by the radically new and brilliant ideas behind QV, knowledge-extractable voting bases decisions on something which is sparse and better suited for blockchain applications — namely knowledge — to achieve a decision (partially) independent of wealth. As opposed to wealth knowledge is acquired through experience or education by perceiving, discovering, or learning. It can’t be bought on an exchange. It can’t be transferred from a knowledgable to less-knowledgable or wealthy person. Moreover, knowledge is non-fungible, as knowledge relates to a particular field of interest and expertise.
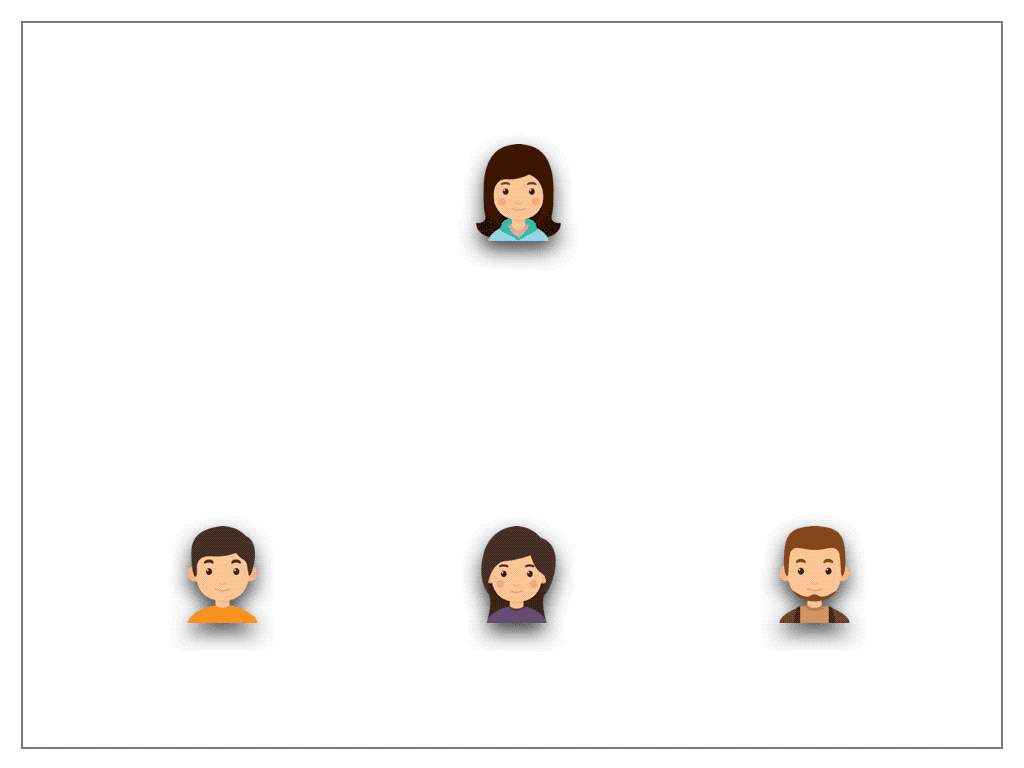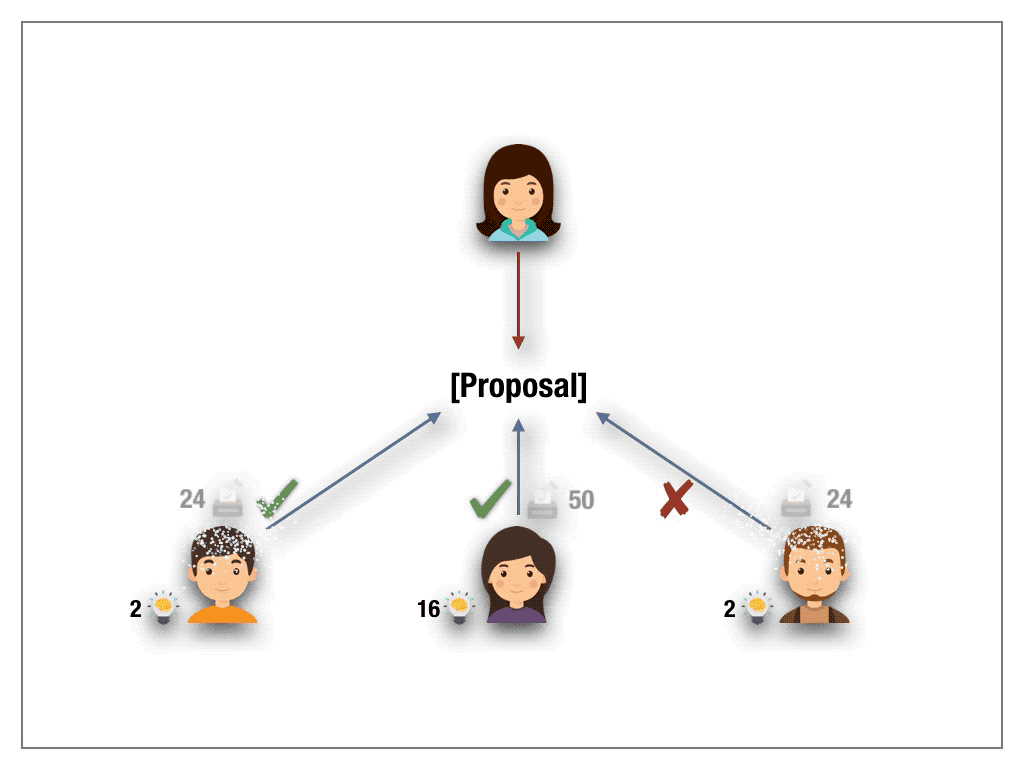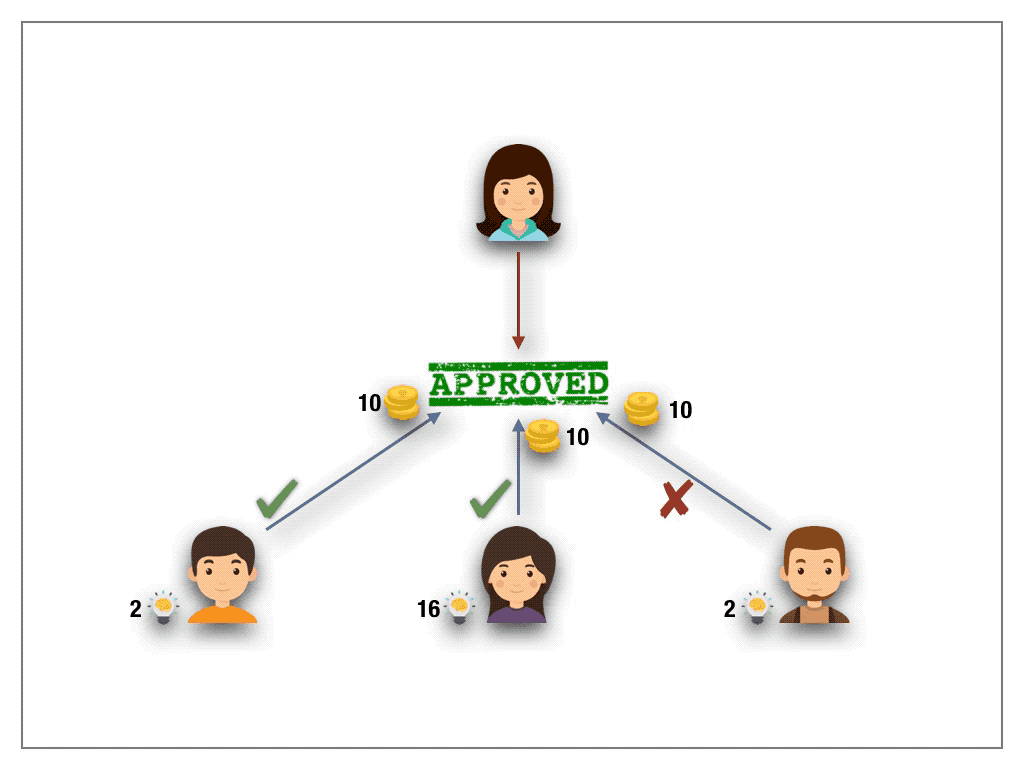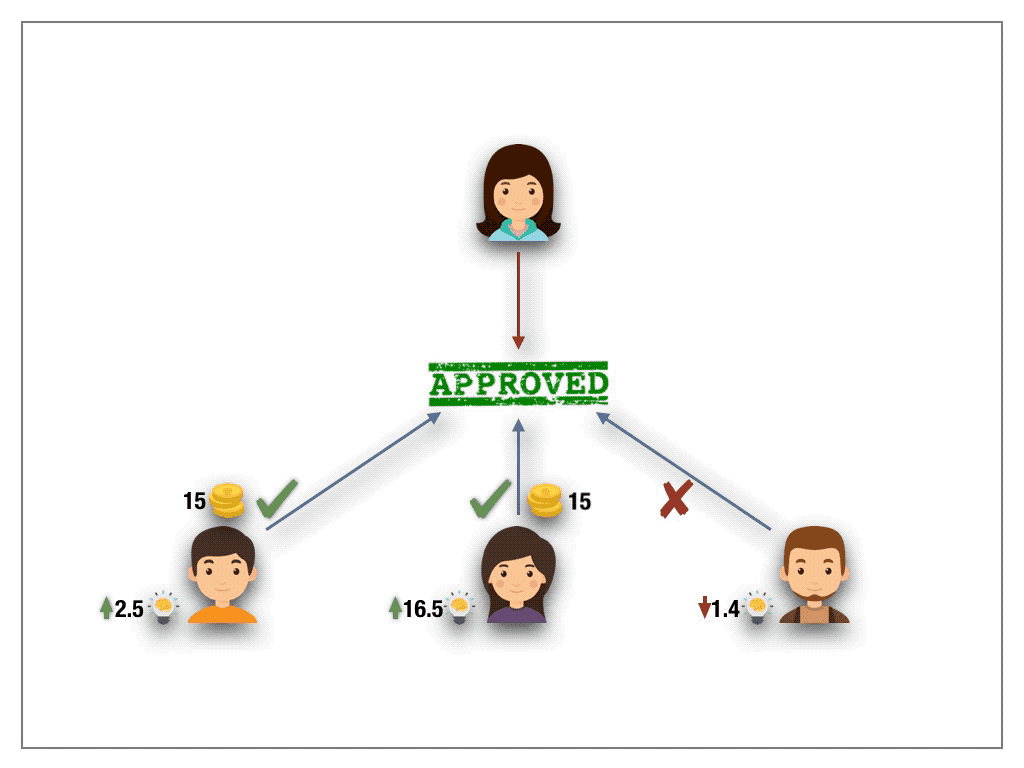
Knowledge-extractable voting adds to the mechanics of 1s1v protocols a second token, called the knowledge token. A crucial property of knowledge tokens is that they are non-purchasable and non-transferable. The only way to mint knowledge token is to contribute in votings and comply with the decisions of the quorum. If the voter deviates in a ballot from the quorum decision then not only his stake is slashed but also the voters’ knowledge tokens are drastically burned (to the square root). Hence an increased number of knowledge tokens in a particular field allows to quantify the expertise of the voter. It is this expertise that is taken into account to weight the power of the voter in the ballot.
4. Conclusion
Voting schemes are for the stability of DAOs as vital as consensus protocols are for the blockchain network. Looking at the impact voting schemes have for DAOs, it is of crucial interest to understand the security guarantees they provide for blockchain-based applications. We analyzed the suggested voting protocols and concluded that diligence and care must be taken when choosing the right voting scheme. We compared the de-facto voting protocols and concluded that knowledge-extractable voting is an attractive candidate to overcome richer-get-richer attacks on the blockchain. This implies resistance against Sybil attacks a property other stake-based voting schemes fall prey.
Acknowledgement
This is joint work with Marvin Kruse and all animations are his courtesy.
2019 is the year of DAOs was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
from Hacker Noon https://hackernoon.com/2019-is-the-year-of-daos-9728618873f5?source=rss—-3a8144eabfe3—4
